The demand for continuous integration and IaC deployments has been sky-high in recent years. This level of functioning has also demanded scalable and consistent automation. Infrastructure as code (IaC) is absolutely important in cloud environments. It helps avoid any cloud deployment irregularities, thus saving the DevOps engineers enough time for productivity. IaC deployments are popular today, for the fact that they automate the IT infrastructure provisioning process, instead of tedious, manual on-premise processes. With a combination of Infrastructure as Code and adoption of Infrastructure as a Service (IaaS), companies would be able to significantly reduce their cloud costs while running scalable cloud implementations.
IaC deployments must be secured at all times
IaC deploys and succeeds in IT infrastructures, including network servers, databases, virtual machines, and services. It is a key DevOps exercise that strengthens agile software development along with continuous delivery. IaC supports speed development and efficient management of IT infrastructures. To configure individual deployment environments without IaC, IT teams and developers should always follow up and be on the same page to avoid any inconsistencies in their deployments. However, manual processing in deployments often lead to irregularities and security concerns.
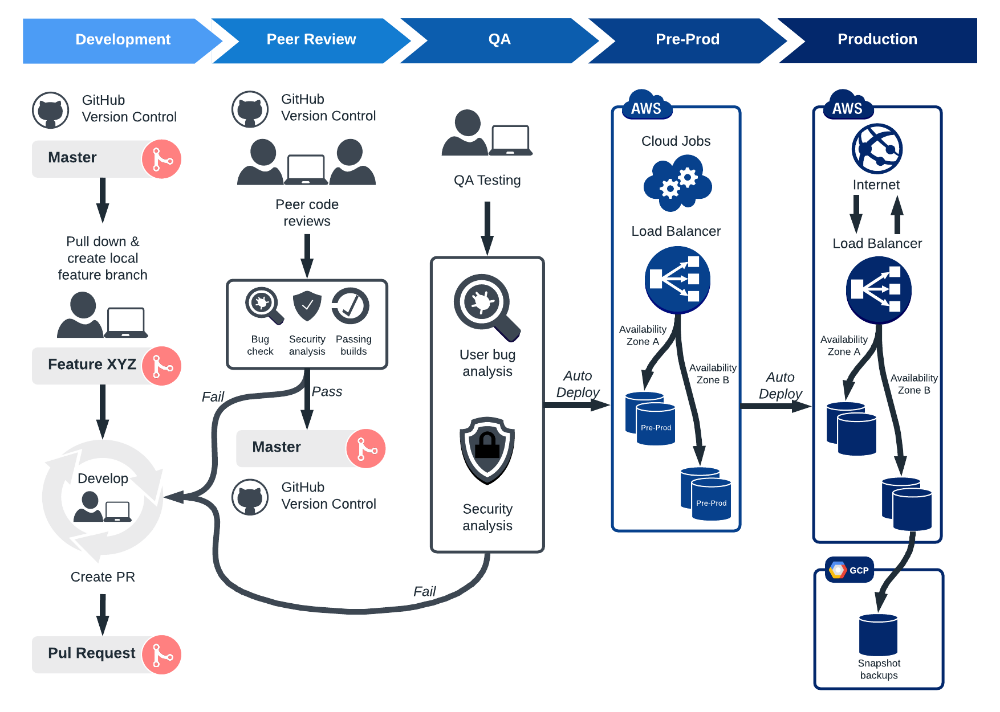
Workflow to ensure security and compliance of IaC deployments
IaC well defines the Infrastructures within code file. Users should specify multiple properties but this might lead to insecure deployments due to poor implementations. In cloud environments, misconfigurations with IaC tools are still a major security concern. Entire infrastructure could be breached and compromised with the security loopholes in the Infrastructure as Code pipeline.
To secure public cloud and hybrid environments, the following measures are recommended:
Implementation of the principle of least privilege
Any user, process, or program will have the only minimum privilege to perform the function. For instance, to grasp the records from a database a user account is created. This functioning does not require admin rights. Similarly, if the programmer is working with legacy code updating lines, then access to financial records is not needed. This principle of least privilege is also known as principle of least authority (POLA) or principle of minimal privilege (POMP). This principle is referred to as best practice in IT information security-related functions because the principle of least authority gives the user only the required access to execute the job.
Here’s an example of Encryption in Transit by Default in Google Cloud Platform:
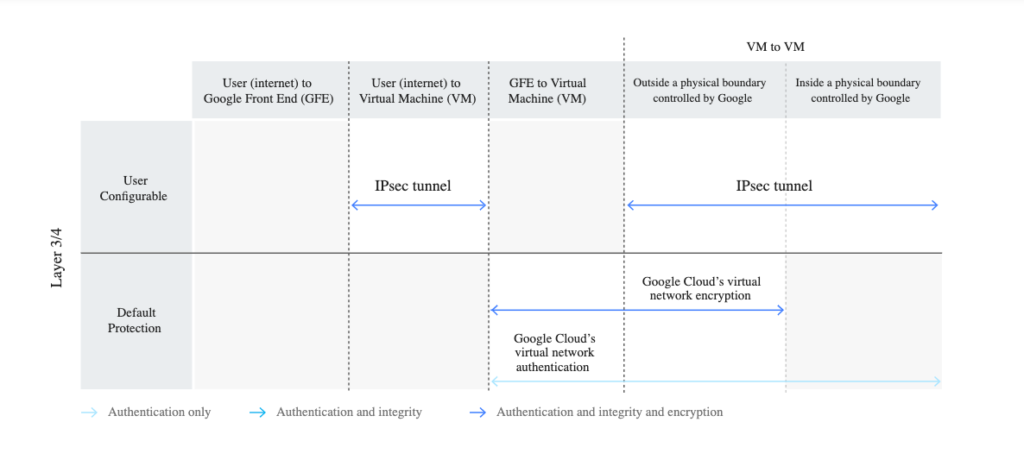
Companies usually are prone to data risk because they lack IT policies and recognition of industry standards to execute security control on data like HIPAA, PCI, ISO 27001 and GDPR. To secure the data in transition, the best strategy is to implement a multi-layer plan. Eventually, identify user’s technology and industry standards should utilize PCI, GDPR etc.
The biggest element in securing data-in-transition is recognizing the risks and the frequency of risks. The basic steps in identification of security threats are consideration of departments, people and data of security lifecycle. Define priorities for ensuring the security of critical assets from vulnerabilities. Thus, to secure data, refer risk management and planning as top-level approval steps.
Audit logs
Plan the risk management and use audit logs to assess the security risks of classified and sensitive assets and in the identification of root causes of various incidents. Audit logging services help in tracking who is doing what, when, where in the cloud infrastructure. Provisioned cloud infrastructure supports audit logging and it is also easy to omit the provisioning feature through code. Frequent security checks and threat identification would be feasible through audit logs. Update IT infrastructure to the latest version of the software.
Apply security patches whenever applicable. Moreover, do not expose the central server on the internet to restrict the spread of compromise to other elements downstream. Add a real-time element that identifies misconfiguration in service providers to ensure protection in the pipeline. An auto-remedy function can help in the identification and rectification of failures.
Securing the IaC deployments ensures uniformity in data processing on public cloud and public cloud throughout the whole delivery process. It ensures quality and an increase in environment provisioning and configuration speed. Developers will have more productive time to develop new features and meet customer demands better. Because better product service means better customer satisfaction.
In conclusion, the future of IaC lies in securing the codes. As long as businesses move to the cloud, IaC will remain as an important cog in the IT wheel. DevOps engineers must integrate the security aspects right at the beginning of the project to their CI/CD pipelines to ensure strict security and for the workloads.
On that note, run a free security audit to check your infrastructure security. Call us or get in touch with us. Let’s run cloud workloads more securely!
Give enough access to perform a task to maintain secure IT infrastructure. Attackers can’t access complicated IT systems or sensitive information by compromising the most vulnerable user device, account or application. Implementing this principle can restrict further containment of security layers in the infrastructure. As a result, infrastructure hack at large could be prevented. Particularly, when connected with public cloud providers, account privileges in cloud services should be minimum. Restrict access to tools and permissions by controlling the foothold in nodes.
Use IaC deployments security plug-ins
Mitigate the potential issues with IaC templates by linking security plug-ins in the integrated development environment (IDE). Such IaC security plugins are Prisma Cloud Plugins for configuring popular IDEs that include VScode, IntelliJ. Install and configure security plug-ins for CI/CD tools like DevOps, Azure, Jenkins and CircleCI, and Source Control Management systems like Github. Develop and deploy plugins into the current workflows to reduce friction and improve the scanning and fixing issues of security issues. These plugins do not need any additional tools in identifying and fixing the potential issues.
PrismaTM is the comprehensive native security plugin that perfectly integrates with cloud environment. Plugins provide industry’s broadest compliance coverage and security for applications, data, users and entire cloud technology stack. Security is provided cross multi and hybrid cloud environments. These plugins also function throughout the lifecycle without ambiguities.
Prisma Cloud DevOps enables security teams and DevOps to scan any insecure configurations in the IaC templates. Moreover, spot vulnerabilities and security patches in container images before deploying the resources in runtime environments.
Other IaC templates are HashiCorp Terraform templates (HCL format), AWS Cloud Formation Templates (JSON or YAML format), Kubernetes App manifests (JSON or YAML format), or Helm Charts. These tools focus on helping the DevOps engineer to monitor any misconfigurations that could give rise to cyber security of the IT infrastructure, be it in public cloud or the hybrid cloud.
Encryption Coverage
Most of the cyber-attacks happen at the data transfer stage from one location to another. If the data is sensitive, then encrypt the data before transiting. Use Transport Layer Security for encrypting data that is in transition. Furthermore, data transfer requirements include strong authentication, rules and policy management, automation of file-based tasks guaranteed to deliver, user Ad Hoc secure file transfers, and integration with security controls. Additionally, inspect data continuously and protect through routine security scans and alert notifications, monitoring the file transfer activities, tamper-evident audit trail, automated report creation, automated distribution, report availability and, disaster recovery.
Here’s an example of Encryption in Transit by Default in Google Cloud Platform:

Companies usually are prone to data risk because they lack IT policies and recognition of industry standards to execute security control on data like HIPAA, PCI, ISO 27001 and GDPR. To secure the data in transition, the best strategy is to implement a multi-layer plan. Eventually, identify user’s technology and industry standards should utilize PCI, GDPR etc.
The biggest element in securing data-in-transition is recognizing the risks and the frequency of risks. The basic steps in identification of security threats are consideration of departments, people and data of security lifecycle. Define priorities for ensuring the security of critical assets from vulnerabilities. Thus, to secure data, refer risk management and planning as top-level approval steps.
Audit logs
Plan the risk management and use audit logs to assess the security risks of classified and sensitive assets and in the identification of root causes of various incidents. Audit logging services help in tracking who is doing what, when, where in the cloud infrastructure. Provisioned cloud infrastructure supports audit logging and it is also easy to omit the provisioning feature through code. Frequent security checks and threat identification would be feasible through audit logs. Update IT infrastructure to the latest version of the software.
Apply security patches whenever applicable. Moreover, do not expose the central server on the internet to restrict the spread of compromise to other elements downstream. Add a real-time element that identifies misconfiguration in service providers to ensure protection in the pipeline. An auto-remedy function can help in the identification and rectification of failures.
Securing the IaC deployments ensures uniformity in data processing on public cloud and public cloud throughout the whole delivery process. It ensures quality and an increase in environment provisioning and configuration speed. Developers will have more productive time to develop new features and meet customer demands better. Because better product service means better customer satisfaction.
In conclusion, the future of IaC lies in securing the codes. As long as businesses move to the cloud, IaC will remain as an important cog in the IT wheel. DevOps engineers must integrate the security aspects right at the beginning of the project to their CI/CD pipelines to ensure strict security and for the workloads.
On that note, run a free security audit to check your infrastructure security. Call us or get in touch with us. Let’s run cloud workloads more securely!
[/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]






Recent Comments